OAuth
OAuth 2.0 based authentication allows your users to login to your CloudShark Enterprise server via either Google, GitLab, or Okta. This simplifies the work of an Administrator by eliminating the need to create user accounts or reset passwords if they are forgotten. CloudShark accounts can be created when a user logs in for the first time and default CloudShark settings can be configured using the User Default Settings.
Okta
The Okta authentication method supports configuring a custom base URL and makes group membership available via OAuth. Okta is also supported as a SAML 2.0 authorization endpoint if you would prefer to do it that way.
Configure Okta
Authentication via Okta requires your Okta admin to create a new “app integration” within your domain for your CloudShark Enterprise server. You can follow the Okta documentation here.
- Choose “OIDC - OpenID Connect” as the sign-in method
- Choose “Web Application” as the Application type.
General Settings:
- “Authorization Code” is the only option that needs to be selected for Grant type
Sign-in redirect URIs
A single sign-in redirect URI should be configured in Okta to match the
URI for your CloudShark Enterprise system with the path set to
/auth/okta. For example: https://cloudshark.my.corp.lan/auth/okta.
We do not recommend allowing a wildcard in the sign-in URI redirect.
Sign-out redirect URIs are optional and should be removed.
Assignments
The assignments section is specific to your organization.
Making Group membership available
In order for Group memberships to be available in CloudShark, you must update the Application within Okta to send them.
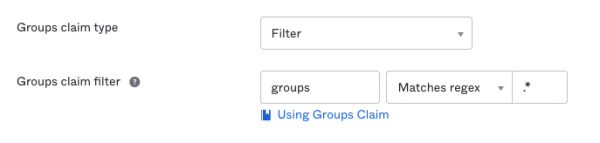
After saving and creating the application, visit the “Sign On” tab for your new application integration. Edit the section labeled “OpenID Connect ID Token”. You must configure a Groups Claim in order for group membership to be available within CloudShark.
If you do not have specific group requirements, change the groups claim filter to be “groups”, “Matches regex”, “.*” as shown here:
Configure CloudShark
Once you have created the application in Okta, move to CloudShark to finish setting it up.
Configure the BaseURL for your Okta org. It will be something like https://${myBaseUrl}.okta.com. Once that is configured, click the “auto-discover endpoints” link to fetch your organizations Authorize and Token URLs.
Copy the following from Okta into CloudShark:
- Client ID
- Client Secret
Note: CloudShark does not support using a Public/Private key for Client authentication.
Groups
If you want Okta group membership to map to CloudShark groups, please read our External Authentication documentation under the “Managing External Groups” section.
Testing
Press “Save settings” on the External Authentication settings page. You are now configured to log your users in via Okta. To test, log out and verify that there is a new “Login with Okta” button on the sign-in page. Clicking it will start the authentication exchange to log you in.
Instructions for generating Client ID and Client Secret for OAuth with Google
When Google is used to authenticate users for CloudShark their e-mail address will become their username.
If you are using a work domain with google you can specify a Domain to restrict users to your domain. This will require that the user uses an e-mail address that is a part of the specified domain.
Google requires that the host-name in the Callback URL is able to be resolved using a public DNS server.
GitLab
Log-in to CloudShark via GitLab by setting up GitLab as an OAuth 2.0 identity provider.
If you are using a shared GitLab instance, you can specify a group that the GitLab user must belong to in order to be allowed to log into the CloudShark Enterprise system. If this is not specified, then anybody who can log into GitLab can also log into CloudShark Enterprise.
GitLab has the concept of a “username” as well as an email address. CloudShark lets you pick which you’d like to use for the CloudShark username. To use an email address, the user must have this set as the Public email in their GitLab profile.