Threat Assessment
The Threat Assessment analysis tool in CloudShark uses Suricata to generate threat vectors based on the network traffic in a PCAP file. Each threat vector consists of one or more alerts generated by a collection of Suricata signatures known as a ruleset.
Watch this video to see the Threat Assessment analysis tool in action!
From the Suricata website:
Suricata is a free and open source, mature, fast and robust network threat detection engine.
Suricata inspects the network traffic using a powerful and extensive rules and signature language, and has powerful Lua scripting support for detection of complex threats.
To open Threat Assessment, choose it from the Analysis Tools menu when viewing a capture. A summary showing the number of alerts generated by severity is displayed. Clicking on a single severity or opening the Advanced Analysis view will display the threat vectors as a ladder diagram view.
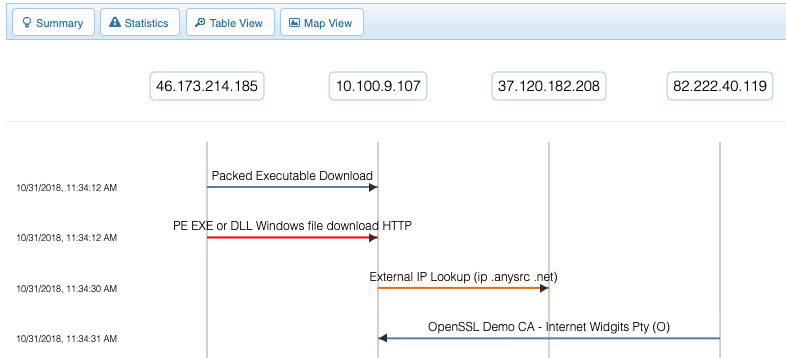
Ladder Diagram
The advanced analysis view displays a ladder diagram showing all endpoints in the capture with alerts associated with them along the top. Each threat vector is displayed below as a line between two endpoints, with an arrow indicating the direction of the threat vector.
Endpoints can be dragged to move them horizontally or dragged off to remove any threat vectors associated with them from the ladder diagram. The following filters in the upper right can also be used to control what threat vectors are displayed by:
- Severity
- Category
- Signature
CloudShark encodes the position of the endpoints and any filters set in the URL for easy sharing. Copying and pasting the current URL will preserve this specific view.
Threat Vector Details
Clicking on a specific threat vector from either the ladder diagram view or the table view will open the Threat Vector Details. In this view, you will find the time, which packet triggered the threat vector, and the associated endpoints. There are links to additional threat vectors triggered by the same source, destination, or IP pair.
Below this is a list of all the alerts that were triggered. Clicking on an individual alert will display the Suricata signature source. Below the list of alerts are links to any of the external references included by the Suricata signatures that triggered the alerts.
In the bottom-left corner is a link to the Follow Stream analysis tool showing the entire TCP, UDP, or HTTP stream that triggered the threat vector.
Statistics
The statistics view displays the alerts grouped by the following:
- Severity
- Category
- Signature Name
- Alert Source and Destination
- Alerts by Country
Clicking on an individual statistic will open the ladder diagram view with a filter applied matching what was selected.
Map View
The map view uses the MaxMind GeoIP2 database to generate a world map color-coded by the alerts generated by a PCAP file. Clicking on an individual country will open the ladder diagram view filtered for threat vectors by the selected country.
Table View
The table view will display all of the alerts triggered by the PCAP file. These can be sorted by column by clicking on the column header. Clicking on an individual row will display the threat vector details containing the alert.
Troubleshooting
If an error message is displayed when Threat Assessment is selected from the Analysis Tools menu or the Statistics View fails to display correctly, the following may help resolve your issue. If not, please contact QA Cafe Support and we will be happy to help!
Failed connect to localhost:8989; Connection refused
If clicking on the Threat Assessment analysis tool displays this error, Suricata may still be starting up behind the scenes. Try opening Threat Assessment again, and if you continue to see this error, please contact support for assistance.
CloudShark::Suricata::UnsupportedFileType
Suricata requires the file type to be either pcap or pcapng, other file types such as a compressed gzip file are not supported by the Threat Assessment analysis tool. A capture file can be downloaded as a new pcapng and uploaded to CloudShark if it is not one of these types.
The file encapsulation must also be one of the following:
EthernetNULL/LoopbackLinux cooked-mode captureRaw IP
Other file encapsulation types such as IEEE 802.11 plus radiotap radio header,
commonly found in Wireless captures, are not supported.